Security Challenges in the Popularization of MCP Services
This article was first published on our team’s. Click here to read the Chinese version. https://mp.weixin.qq.com/s/M2M8XsEFmT7rrs1M5gJ9hw
1. Introduction.
MCP (Model Context Protocol) is an open protocol launched and open-sourced by Anthropic in November 2024, aiming to realize a seamless conversation between AI and external tools. With the popularity of MCP, its applications have been expanding from browser operations to database querying, from weather information acquisition to complex system integration, which greatly enhances the practical value of AI. However, against the background of this rapid development, some potential security issues gradually emerge.
2 Research background
The core value of MCP, as a protocol framework specialized in realizing the interaction of large-scale language models with external tools and data sources, is to securely realize the invocation of AI models to external tools, the access to databases, and the execution of specific tasks. However, this powerful extension of functionality comes with corresponding security risks.
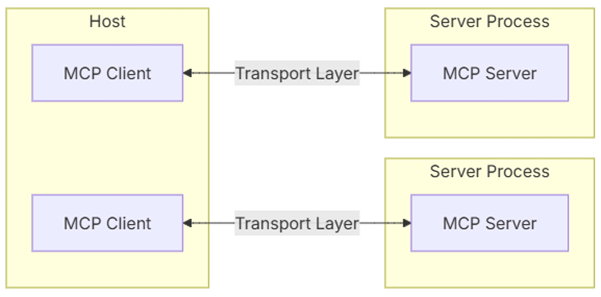
MCP provides two main communication modes that allow AI models to flexibly interact with external tools:
The first is the local communication mode, which is like two programs “talking” on the same computer, passing information through standard inputs and outputs. For example, if you run an AI application locally, it can directly call a tool or program on your computer, which is fast and secure.
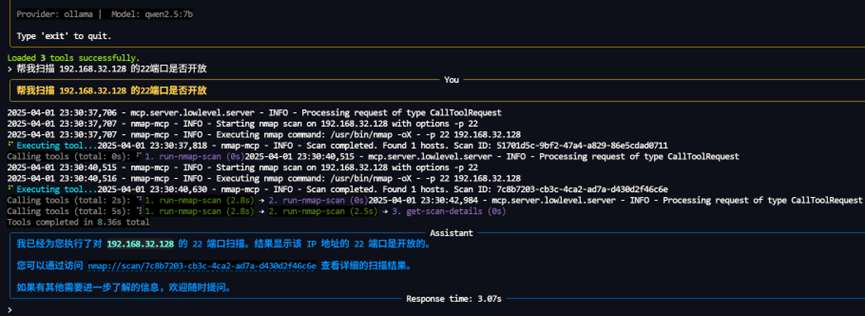
Look at a practical example: with the MCP protocol, we can make it super easy for AI to use various tools. For example, we can get an nmap service based on MCP and set up the communication mechanism in the local environment. After setting up the communication mechanism, the locally running AI can directly call the nmap tool and easily complete the network port scanning.
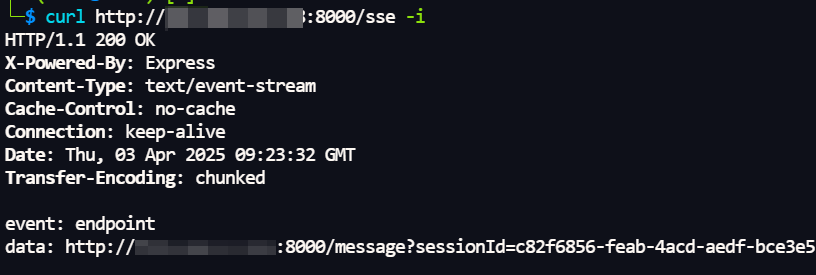
The other is the remote communication mode, which is more like the AI “chatting” with the remote tool through the network. It uses SSE (Server-Sent Events) + HTTP protocol technology, which allows the AI to receive data streams from remote servers in real time. This approach is particularly suitable for scenarios that require access to cloud resources or use in distributed systems.
The existence of these two communication methods allows MCP to be better adapted to different usage scenarios.
3 Research Methodology
3.1 Feature Extraction
The rapid emergence of MCP services provides us with rich samples for analysis. A variety of MCP service implementations exist on GitHub, and we focus on two categories: one is MCP servers implemented based on NodeJS (e.g., Supergateway), and the other is services implemented based on Python (e.g., MCP-proxy, Markitdown, etc.). Of course, there are other implementations, but this study will focus on these two categories.
The response of a NodeJS-based implementation of the MCP service when accessed directly is as follows:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
HTTP/1.1 404 Not Found
X-Powered-By: Express
Content-Security-Policy: default-src 'none'
X-Content-Type-Options: nosniff
Content-Type: text/html; charset=utf-8
Content-Length: 139
Date: Thu, 03 Apr 2025 08:51:33 GMT
Connection: keep-alive
Keep-Alive: timeout=5
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Error</title>
</head>
<body>
<pre>Cannot GET /</pre>
</body>
</html>
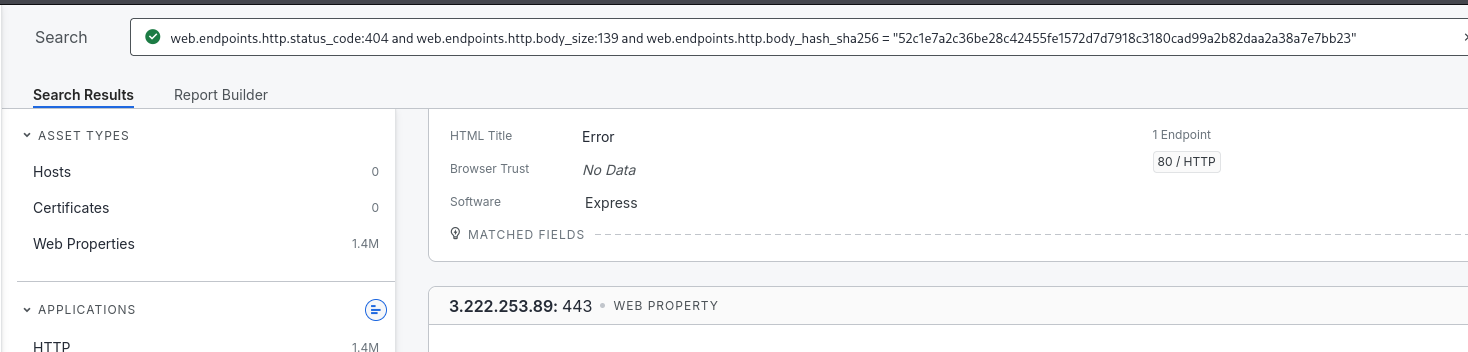
Based on this response, we can summarize the search syntax for a specific spatial mapping system (e.g., Censys):
web.endpoints.http.status_code:404 and web.endpoints.http.body_size:139 and web.endpoints.http.body_hash_sha256 = “ 52c1e7a2c36be28c42455fe1572d7d7918c3180cad99a2b82daa2a38a7e7bb23” This search method is not 100% sure that the result is the MCP service, but it does help us to narrow down the search effectively.
Similarly, the response of the MCP service developed based on Python is as follows
1
2
3
4
5
6
7
HTTP/1.1 404 Not Found
date: Thu, 03 Apr 2025 09:03:06 GMT
server: uvicorn
content-length: 9
content-type: text/plain; charset=utf-8
Not Found
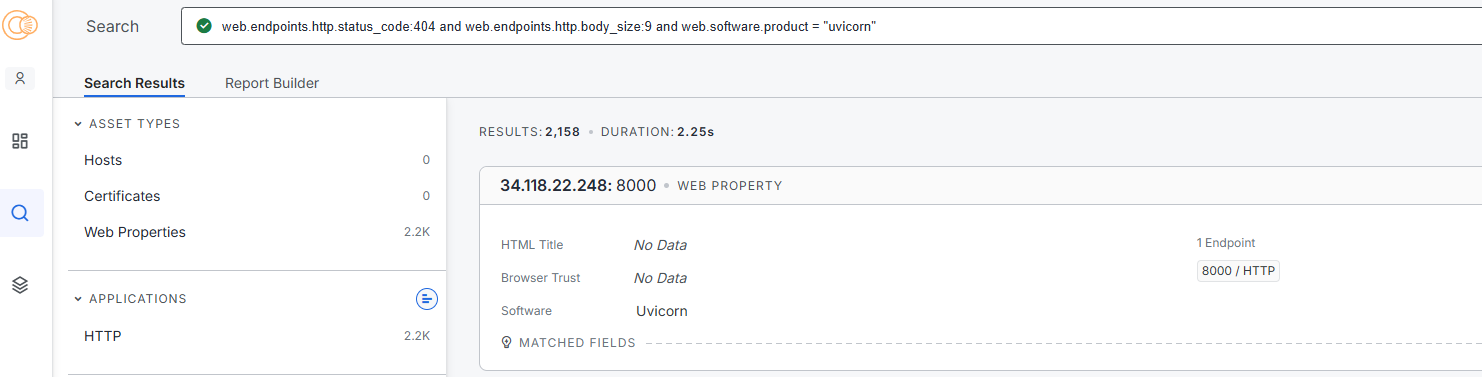
Based on these characteristics, the following search syntax can be constructed:
web.endpoints.http.status_code:404 and web.endpoints.http.body_size:9 and web.software.product = “uvicorn”
Due to the short public availability of the MCP, we extracted nearly a week’s worth of assets from cyberspace search engines based on the above search syntax. Next, we performed a scan based on publicly available SSE paths (e.g., “/sse”, “/mcp”, or “/mcp-sse”, etc.).
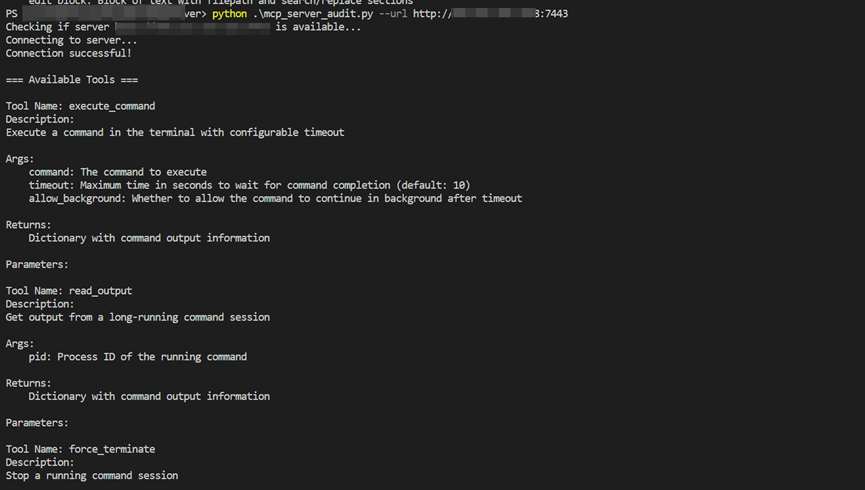
Then, we utilize MCP’s Python SDK https://github.com/modelcontextprotocol/python-sdk to implement a client to connect to the remote MCP service for a list of available tools.
4 Research Findings
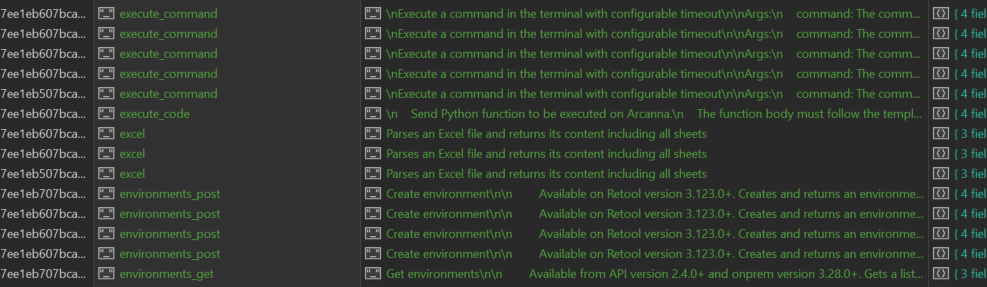
Based on the above methodology, we found unauthorized MCP services on the Internet, from which we extracted 4,327 methods available for AI calls.
Through in-depth analysis, we found that the types of tools provided by these services cover a wide range of areas, from basic system operations to sensitive data access. We categorized these tools and the following table details the distribution of tool types:
| Category | Name | Percentage |
|---|---|---|
| calendarGmailTools | Calendar and mail related | 19.9 % |
| tenantBrandTools | Tenant and brand management tools | 17.4 % |
| searchRetrievalTools | Web Search and Retrieval | 8.7 % |
| fileContentTools | Document and Content Processing | 6.8% |
| systemTools | System and Command Line | 6.8 % |
| memoryTools | Memory and Storage Related | 6.2% |
| mathTools | Math and Computing | 5.6% |
| taskManagementTools | Task and course management tools | 5.6 % |
| healthUtilityTools | Health checks and utility tools | 3.7 % |
| databaseTools | Databases and Queries | 3.1% |
| securityTools | Security and Encryption | 3.1% |
| otherTools | Other/Uncategorized Tools | 1.9 % |
| webCrawlingTools | Web crawlers and content acquisition | 1.9% |
| jiraTools | Jira-related | 1.2% |
| financialTools | Finance and Account Management | 1.2% |
| aiRecommendationTools | AI and Recommendations | 1.2% |
| ticketApplicationTools | Work Order and Application Status Tools | 1.2 % |
| notificationTools | Notification and Email Tools | 0.6 % |
Based on the analysis of the data in the table, we can draw the following key findings:
- Top tool categories: Calendar and mail-related tools (19.9%) and tenant and brand management tools (17.4%) accounted for the largest share, totaling more than 37% of the tool distribution.
- Information Processing Tools: Web Search and Retrieval (8.7%), File and Content Processing (6.8%), and System Tools (6.8%) formed the second tier, reflecting basic functionality needs.
- Technical Support Tools: Memory and Storage (6.2%), Math Computing (5.6%), and Task Management (5.6%) form a medium-sized category of tools.
- Specialized Domain Tools: Health Checks (3.7%), Databases (3.1%), and Security Tools (3.1%) are smaller but show the potential for MCPs to be used in specific domains.
- Niche Application Tools: Tools in categories including web crawlers, Jira tools, and financial management all account for between 1-2%, indicating that MCP services are expanding into more specialized and niche areas.
This distribution indicates that MCP services are currently focused on daily office and system management, but have begun to penetrate into various specialized fields. Therefore, the security of MCP becomes especially important. With the diversification of tool types and the expansion of application scenarios, unauthorized access to these services may lead to security risks such as leakage of sensitive information and misuse of system resources.
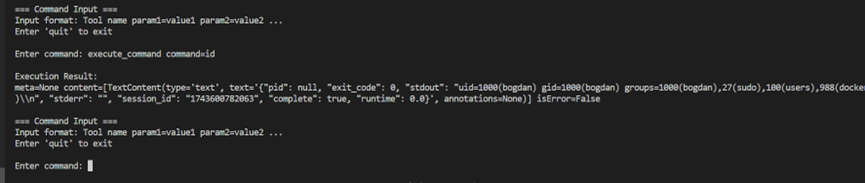
For example, the execute_command tool can execute commands directly on the target system
6 Conclusion
Based on our findings, MCP services face serious security challenges along with their rapid popularity. The exposure of unauthorized MCP services to the Internet may not only lead to the leakage of sensitive information, but also be exploited by attackers to execute malicious commands, posing a significant threat to the information security of an organization. Therefore, we strongly recommend MCP service providers to strengthen access control, implement authentication, conduct regular security audits, and establish a comprehensive security response mechanism.
In addition, MCP has recently (2025/03/26) released an important update
This update contains two key changes:
1. New Authentication Framework
MCP introduces a comprehensive authentication framework based on OAuth 2.1, which significantly improves security. The new authentication mechanism provides standardized access control and supports a variety of authorization processes to effectively prevent unauthorized access and potential security threats.
2. Transport Protocol Improvements
The protocol adopts a more flexible Streamable HTTP transport instead of the original HTTP+SSE method. This improvement not only enhances the scalability of the protocol, but also improves compatibility with modern web infrastructures, making it easier to deploy and maintain the service.
These updates precisely address the security challenges we have previously identified, especially in the areas of access control and service authorization, which will significantly reduce the risk of unauthorized access.
7. Reference
- https://spec.modelcontextprotocol.io/specification/2025-03-26/changelog/
- https://modelcontextprotocol.io/docs/concepts/architecture
- https://github.com/supercorp-ai/supergateway/tree/main
- https://github.com/sparfenyuk/mcp-proxy
- https://github.com/microsoft/markitdown/blob/main/packages/markitdown-mcp/src/markitdown_mcp/main.py
- https://github.com/chaitin/SafeLine/blob/695c438ec31f4170920c9903df447f4823dc958f/slmcp/server.py#L43
- https://github.com/modelcontextprotocol/python-sdk